Security Audits & Technology Reviews
Security Audits Identify Gaps & Vulnerabilities to Enable Security Planning.
Physical Security is Essential
Security is one of the most important factors in successful businesses from small start-ups to major global enterprises. With risks and threats changing constantly, organisations need to have theirprotective security measures
up to date and resilient enough to protect against reasonably foreseeable disasters, both deliberate and natural.Security policies, procedures and technology combine to be the first line of defence against the disruptive risk of intruders, thieves, and persons seeking to cause harm or damage for whatever reason and jeopardizing these defense mechanisms can make your business or organisation vulnerable to major losses or even litigation, which you certainly want to avoid.
Like many business owners, you are probably thinking how, exactly, to go about making sure that my security systems and procedures are up to standard and fit for purpose. The answer? Conduct a
physical security audit.
Use a Security Audit to Combat Risks
Like the name implies, a security audit is a comprehensive physical inspection and evaluation of every aspect of your security systems and their parameters throughout your space or facility. This should be carried out on both an individual and macro level by a qualified and licensedSecurity Consultant.
The purpose of an audit is to establish whether the existing security measures, systems, policies, operating procedures, and technology are in place, fit for purpose and functioning correctly. It can also determine if mandatory requirements or codes of practice are being met consistently, thus giving you the information you need to make better decisions about how to protect your people and facilities from harm.
It is the first tool in combating and mitigating the various threats and risks to life and property. We are referring to a broad range of risks and threats not limited to the following:-
- Theft (Internal and External)
- Burglary
- Vandalism
- Workplace Violence
- Transport Fare Evasion
- Graffiti
- Workplace Drug and Alcohol Abuse
- Terrorism
- Fraud
- Arson
During the
audit
process, we define known or looming threats and determine if the current systems and measures can withstand the risks that emanate from the threats. This is done by using a simple matrix to develop a score that results from multiplying the probability of an event with the consequences of it happening.LIKELIHOOD X CONSEQUENCE = RISK SCORE %
The image below shows the matrix with the left-hand column denoting the probability of an event from very unlikely to very likely and the top row showing the consequence of an event from insignificant to critical.
Simply chose one score from the left column and move across to the appropriate consequence score and multiply the two numbers and you have a score to work from, such as the image below.
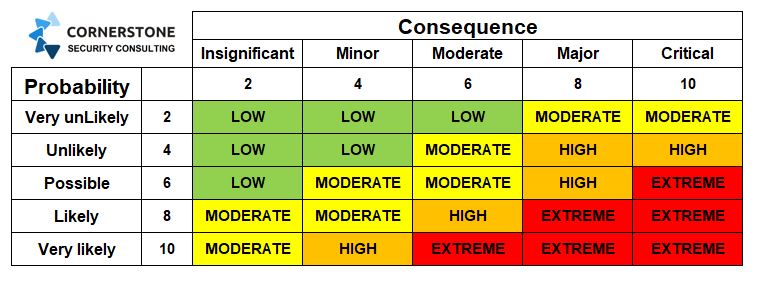
For instance, if the probability of an intruder is low and the consequence of property theft is insignificant the score would be as follows.
Not Very Likely X Insignificant Consequence = 2 x 2 = 4%
Therefore, the risk score is 4% and little, or no, attention needs to be given to protective measures against the risk of intrusion.
However, what if the risk of intrusion was likely to happen and the consequence of theft would be a critical disruption to the business, for say a cash in transit company, then the score would be different.
Highly Likely x Critical Consequence = 8 x 10 = 80%
Is an 80% chance of theft, and loss of trading, worth the risk to that company. The answer is no. Therefore, stringent measures need to be taken to address the vulnerabilities.
With the scores completed we can then prioritize them by severity and then make recommendations for mitigation against the identified vulnerabilities.
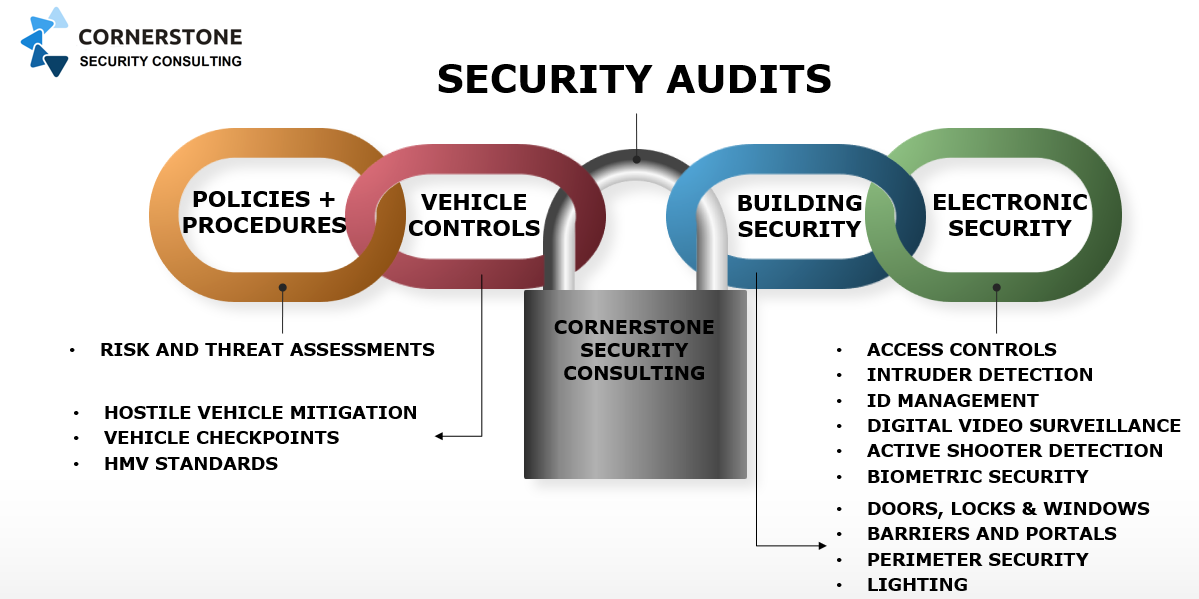
Our
Security Audits
include but are not limited to the following areas and security sub-systems.- Site Security Operations
- Building Construction
- Perimeter Fencing, Gates and Barriers
- Vehicle Checkpoints
- Key Controls and Locking Systems
- External Lighting Arrangement
- Security Control Room
- Post Room Security
- Access Control Systems
- Digital Video Surveillance Systems
- Intruder Detection Systems
- Evacuation & Mustering Systems
- Server & Comms Rooms
- ID Verification & Credential Management
- Internal & Ext. Communication Systems
- UPS Systems
Security Specification Audit
Another type of audit we often carry out is a"Security Specification" audit.
Basically, we are determining if the existing equipment and security systems have been designed and installed to the "original" specification and in line with all relevant Australian standards, codes of practice, and the manufacturer's recommendations.These
audits
usually follow on fromnew security projects
where a construction company is the "client" for the initial stage of the installation prior to handing the finished systems over to the new tenants.Audit Findings and Recommendations
Once the report is completed, we can meet with you to discuss our findings and recommendations. In turn you can have peace of mind knowing that your business, facility, or place of residence is compliant and is safe to work and live in andCornerstone Security
can also be engaged to help implement any or all the recommendations if required.The report remains your property and can be made available in hard or soft copy. If you would like a free assessment on conducting a comprehensive
